Security technology is changing for the better as the container deployment model makes it easier to automate application security. This means that as more enterprises deploy containers to public and private clouds they are able to incorporate security automation into their continuous integration and deployment (CI/CD) pipeline.
Cloud-native container security is a term that describes processes and tools that have knowledge of and integration to the container orchestration and deployment pipeline. By using cloud-native tools, enterprises are able to add continuous container security into the pipeline.
Securing enterprise applications requires a layered security strategy, and container-based applications are no different. However, the rapid pace at which application containers are now being built and deployed, sometimes thousands of times per day, can cause breakdowns in security.
Securing the build - ship - run pipeline
The are many security requirements for continuous container security. These can be applied to the typical container deployment pipeline at the appropriate time. Here’s a summary of the most important ones for each phase.
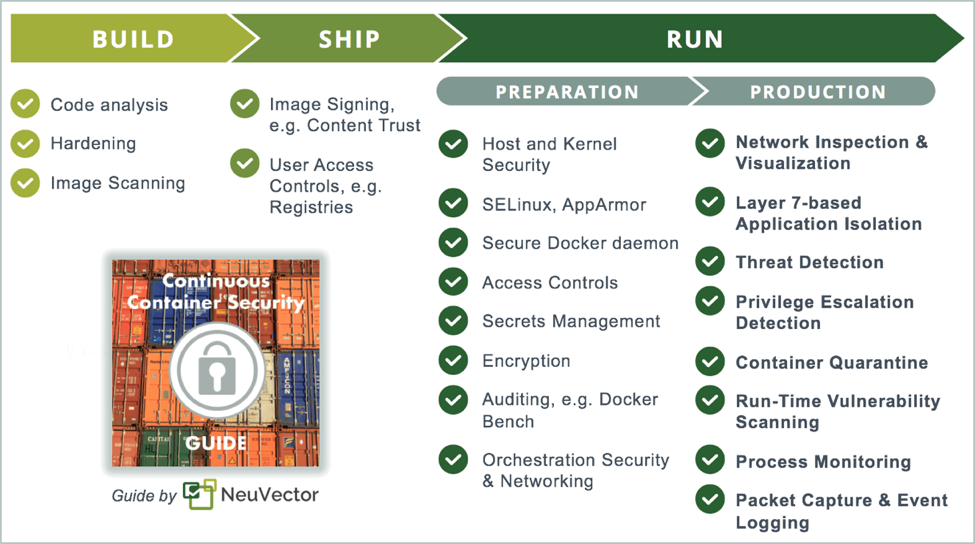
Build securely
The widespread use of open source software in containers increases the risk of vulnerabilities being introduced into enterprise applications. As part of the build phase, software and Docker container images should be scanned for vulnerabilities, and any issues addressed before production. Image registries can be regularly scanned to detect if newly discovered vulnerabilities exist in production ready container images.
Containers are designed to be limited function application services, so any unnecessary packages, libraries and other components should be removed to harden the container and reduce the attack surface.
Ship securely
DevOps teams need to make sure that unauthorized images are not used in production, and that unauthorized people or tools can’t introduce risk into the deployment process. To secure this phase of the pipeline, content trust features such as image signing as well as access controls are required.
Orchestration and container management tools such as Kubernetes, Docker Enterprise Edition, Rancher, and Red Hat OpenShift Container Platform provide many of the security features required in this phase, as well as for some of the ‘preparation to run’ requirements mentioned next.
Run securely
Run-time security is the most important aspect, as applications and systems will be under constant probing and attempted attacks for the lifetime of applications, often years. Even if containers are constantly started, stopped and updated, the hosts they run on are vulnerable to new exploits and zero-day attacks.
It’s critical to prepare the production environment for security first by locking down hosts and using orchestration tools to manage secrets and set access controls. In complex enterprise pipelines it’s critical to segment access by project team as well as team roles.
Once in production, containers can be constantly scaling up, down, and across as well as being updated. This makes it incredibly difficult to get visibility into the network and process behavior of containers. In fact, with the move to a microservices architecture, monolithic applications are being deployed as tens or hundreds of microservices, increasing the potential chaos. This results in the explosion of ‘east-west’ or internal traffic between containers.
For run-time security, a new type of security product called a ‘container firewall’ such as the one from NeuVector is required. A container firewall combines traditional Layer 7 network filtering with cloud-native intelligence to inspect and protect container traffic. Container firewalls are integrated with container orchestration tools such as Kubernetes, Docker Swarm, Rancher and RedHat OpenShift so that protection is maintained as containers scale up, down, or across hosts.
In addition to threat and violation detection, container firewalls are also able to monitor the hosts they sit on as well as container processes for suspicious activity. For example, the Apache Struts exploit recently used in the Equifax breach or a Dirty Cow exploit could allow an attacker to gain control of a host or container and break out of it.
Automation - The way to achieve continuous container security
Although a few companies like Google and Facebook have fully automated deployment pipelines, most enterprises are inching their way toward that goal. But that’s ok. What is important is to map out the pipeline security requirements as outlined above and begin to automate what can be easily done first. Manual processes or traditional scripting can be used to make sure other security requirements are addressed. For example, triggering vulnerability scanning during the build process and periodically for registries is easily automated. The NeuVector container firewall will automatically run Docker and Kubernetes CIS benchmark security tests, scan running containers, and adapt firewall rules as containers scale.
Cloud-native, continuous container security is achievable by all enterprises as they migrate to containerized applications. Understanding how security solutions such as Black Duck, orchestration tools, and the NeuVector container firewall can address the different phases of the pipeline will be critical to enterprise security going forward.
Glen Kosaka is VP Product Management at NeuVector, the Docker Container Firewall company.
Continue Reading
Key findings from “The State of Embedded Software Quality and Safety 2025” report
Aug 26, 2025 | 3 min read
What you need to know about the NIST Secure Software Development Framework
Aug 12, 2025 | 5 min read

