Automate security gates across the SDLC and in CI/CD pipelines without placing additional burden on developers.
Increase developer productivity
Secure code as fast as you write it with fix guidance and secure coding education right in the IDE.
Automate security for efficient DevSecOps
Find and fix issues quickly and at scale with integrated AppSec testing and expanded risk visibility.
Maximize AppSec ROI
Transform AppSec into a business driver with a scalable AST platform.
DevSecOps solutions from Black Duck
Deliver AppSec at the pace of AI
The Black Duck Polaris™ Platform is a cloud-based AppSec testing solution optimized for DevSecOps. Centralize security policies and controls, manage AST testing, and quickly onboard projects and repos to scan code in minutes.
Drive risk detection and remediation
Ensure timely risk detection and rapid remediation with automated AppSec tests across the SDLC and in CI/CD pipelines. Integrate into developer workflows with IDE plug-ins, leading DevOps tools, and universal CI support.
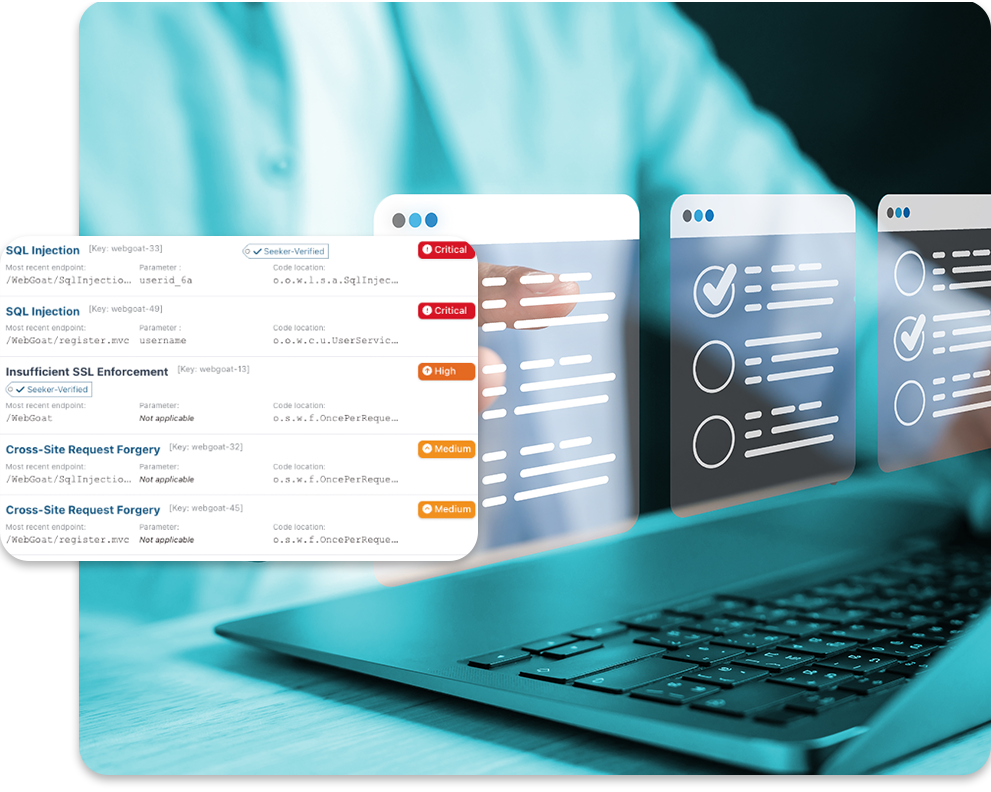
Automate runtime security testing
Turn functional tests into security tests with IAST while monitoring web app interactions in the background. Validate issues automatically, reduce false positives, and support compliance without slowing down developers.
Fix issues faster with AI insights
The integration of Black Duck Assist™ into the Code Sight™ IDE Plug-in provides AI-driven summaries, step-by-step analyses of code, and suggested fixes that developers can use to resolve issues instantly.
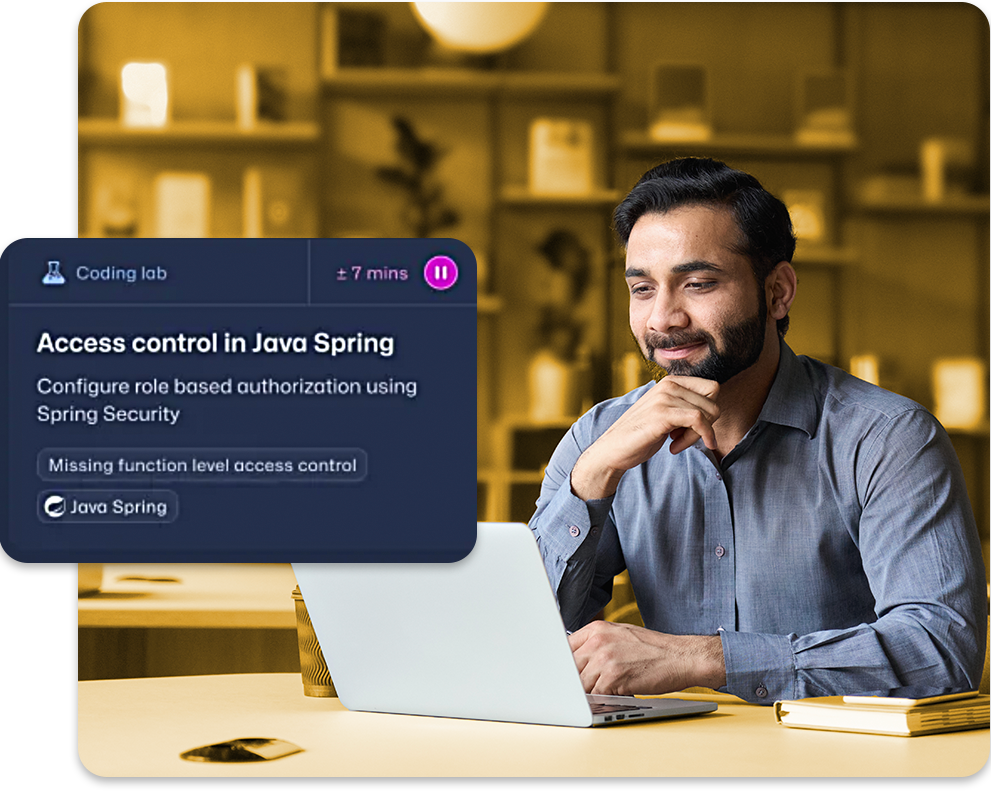
Empower security-capable developers
Tackle security gaps with short, interactive training. Build security-savvy developers with just-in-time, in-context training right in the IDE.
Resources to help you automate DevSecOps
GUIDE
Steps to Evolve DevSecOps at the Speed of AI
Accelerate your AI transformation securely throughout the SDLC
Report
State of DevSecOps Report
Discover tools and strategies to prepare your DevSecOps program for AI code-generation
Webinar
Automate security tests with GitHub, GitLab, and more
Learn how to integrate security testing into CI pipelines
eBook
Expand Risk Awareness in DevSecOps
Learn how to get end-to-end visibility in your DevSecOps program
Frequently asked questions
-
Is it better to use on-premises or hosted security testing tools?When deciding how to deploy an AppSec solution for DevSecOps, it is best to consider the needs of both the security organization and the engineering and operations teams. Often, organizations find that on-premises or hybrid deployments are required only for specific business units or teams. SaaS-based security testing, such as Polaris, can be optimized to scale with DevOps and CI/CD pipelines and minimize costs for DevSecOps. There is no hardware to deploy or software to update, and no limits on team size or scan frequency. Onboard users and applications quickly across your entire organization while leveraging elastic capacity and concurrent scanning across projects and scan types.
-
How do I let developers run vulnerability scans from their IDE?Code Sight integrates security testing for source code and open source components directly into developers’ preferred IDEs, such as VS Code, Visual Studio, IntelliJ, and Eclipse. With Code Sight functioning as a “security spellchecker,” developers can find and fix security defects without switching tools or disrupting their workflow. Code Sight provides developers with detailed fix recommendations at the package and line-of-code level, removing the guesswork from remediation and elevating the developers' security skillset. Additionally, developers can connect Code Sight with other Black Duck solutions, such as Polaris to review issues detected and prioritized by CI/CD pipeline-based scans.
-
Which security tests can I automate with Black Duck?Black Duck has automated solutions for SAST, SCA, IAST, and DAST. These can be integrated and automated in CI/CD pipelines and configured based on predefined policies and workflow triggers. The Polaris Platform provides the flexibility to run the most appropriate analysis engine at the best possible stage in the pipeline based on application, project, schedule, or pipeline events.
-
What’s the best way to structure a DevSecOps program to handle AI-generated code?The security and license issues associated with AI-generated code are essentially the same as those introduced by developers. To prepare for this, define security testing policies up front to automate critical security steps and integrate the appropriate test type at various stages of the SDLC and in CI/CD pipelines. Next, you can automate fix pull requests using DevOps security automation templates like the Black Duck Security Scan GitHub Action, GitLab Template, and Azure DevOps Extension, and deliver clear fix guidance into issue management workflows and the IDE so developers can fix issues faster. These steps help automate and scale necessary AppSec functions at a rate required by AI code-generation.
-
How do I establish security gates without slowing down development or DevOps?It is important that security teams maintain visibility into, and control of, the security risk posture of all the applications and containers that development teams push downstream. To do this in a way that doesn’t impede DevOps workflows, Black Duck's DevSecOps solutions for AppSec testing integrate across the SDLC and in CI/CD pipelines. Trigger scan events, automate prioritization and triage based on policy, and accelerate remediation for more efficient, effective DevSecOps that eliminates vulnerability backlogs. Connect to SCM and CI tools, like GitHub, GitLab, and Azure DevOps, to perform scheduled or triggered scans of proprietary code, open source, and third-party dependencies, and to configure automated actions in response to security policy violations, such as blocking builds, commenting on pull requests, and initiating issue management workflows.