Don’t let defects turn into catastrophes
Your software has to perform as expected for as long as your customers use your products. Adverse conditions and evolving threat landscapes can turn small defects into catastrophic events.
Security and supply chain risks
Functional safety and reliability risks
Costs and complexity of updates
Prevent cyberattacks on IoT devices
Cyberattacks are a significant threat whenever your software connects to the internet. Hackers can exploit security vulnerabilities to access sensitive data or gain control of internal systems. Find and fix coding weaknesses before they are deployed to keep your business and customers safe.
Ship secure and robust software on time
Find and fix issues without slowing down
Coverity® Static Analysis provides fast, accurate code scans with actionable suggestions so your developers and security teams can resolve issues quickly and easily.
See what’s in your software supply chain
Black Duck® SCA identifies all open source dependencies in your software and generates a complete and accurate Software Bill of Materials (SBOM).
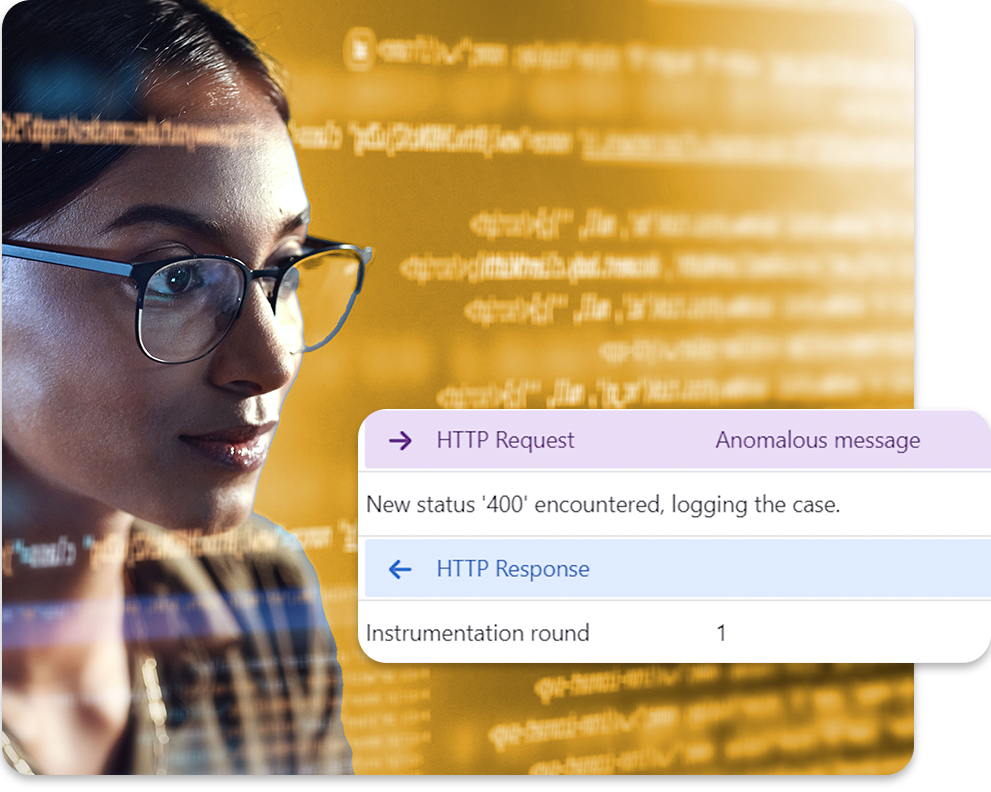
Flag potential zero-day vulnerabilities
Defensics® Fuzzing performs black box fuzzing techniques against your services and protocols to find obscure vulnerabilities before they are exploited, keeping your software resilient and robust.
Demonstrate standards compliance
Black Duck helps track and prioritize issues to keep you ahead of functional safety, security, and industry standards, with native reports to prove compliance.
Deliver high-quality embedded software
Achieving Software Code Compliance
Ensure Reliable and Secure C++ Software
Gartner® Magic Quadrant™ for AST
Build secure and reliable medical device software