Get answers to your hardest AppSec questions
No matter what stage of the application security maturity journey you’re at, you'll have questions. You need to know what’s working, what isn’t, how to get started, how to evolve, and how to thrive.
Let our consulting team help provide the answers.
- How does my security program measure against my peers?
- What steps can I take to improve my security program?
- What does it take to build a world-class AppSec program?
- Do I have clear and actionable security goals?
- Am I doing enough to secure my applications?
- What does a multiyear vision and strategy look like?
Get started with a BSIMM assessment
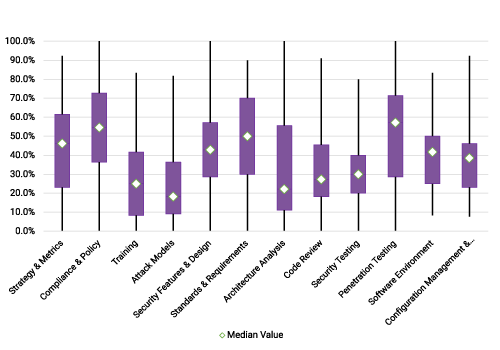
When you participate in a BSIMM assessment, Black Duck provides a scorecard outlining the current state of your full application security program. With benchmarking spanning 4 common domains, 12 practices, and 200+ metrics, it’s easy for you to see how your AppSec program ranks when compared against that of your peers.
- Compare your AppSec program with your peers
- Identify gaps and prioritize change to determine hos to allocate resources and budget
- Develop a strategy based on industry best practices

Maturity Action Plan (MAP)
Align an action plan to your security roadmap
A MAP provides a step-by-step plan with actionable guidance to help you prioritize security program funding, streamline resources, and reduce the overall risks of application vulnerabilities. Each plan delivers a roadmap for security that includes design and implementation guidance for new software security programs (SSPs), open source, CI/CD, cloud, DevSecOps, and more.
- Develop a comprehensive plan to achieve program goals
- Identify necessary resources to successfully execute the plan
- Implement milestones and metrics to measure success

BSIMM: A model for application security success
For over a decade, the Building Security In Maturity Model (BSIMM) report has provided a measuring stick and blueprint to help CISOs and security teams compare the maturity of their programs against those of their peers. Measurements and benchmark data is derived from organizations participating in the BSIMM, so it provides a direct line of sight into the real AppSec program strategies being practiced today. The BSIMM report provides a reference for AppSec maturity assessments, serves as a community for connecting security professionals, and is the driving model to help form remediation action plans.