Subscribe
It’s been great working with Red Hat over the years, as we have brought valuable solutions to our customers, like the Black Duck Connector for OpenShift and the Black Duck Certified Operator. We’re on the lookout for ways to provide more value to our customers by integrating Black Duck application security solutions with Red Hat solutions. One such Red Hat solution we had our eyes on for some time is Red Hat Quay. The Black Duck Connector for OpenShift seemed like a natural fit to scan images that are stored in the Quay container registry. This blog post describes a new feature Black Duck created for Red Hat Quay that is designed to automatically scan images hosted in Quay, triggered through a webhook.
“As we further invest in Quay and Clair to drive greater customer value, we recognize how partner container scanning technologies can enhance and extend Clair’s continuous image vulnerability scanning stored within the Quay registry,” said Julio Tapia, director, Cloud Platforms ecosystem, Red Hat. “We see value in the choice offered by Black Duck, which provides additional metadata sources and actionable, in-depth security information for container images stored within Quay.”
The Black Duck Connector for OpenShift is designed to automatically identify and provide enhanced metadata for open source components in a container image. This is because Black Duck is backed by the industry-leading Black Duck KnowledgeBase™ and multiple types of OSS identification algorithms. The KnowledgeBase contains everything from Linux OS components to application components. The Black Duck Connector alerts users as to vulnerabilities in the images running in their clusters and gives them insight into how attackers could exploit those vulnerabilities. It also provides labels and annotations for pods containing vulnerability counts, policy violation status, and links back into Black Duck.
The typical use case for this integration is when your DevOps and security teams want to ensure that you scan every single deployed container image in your clusters, regardless of origin, using Black Duck. Think about those interesting images that can be deployed in your clusters that you didn’t build or are not part of your CI/CD process. We are now extending this capability to external registries and have built a Quay Image Processor, which allows the integration to scan images that have not yet been deployed into a cluster. Through the use of webhooks, a Quay repository can now be scanned and labeled with a few simple steps.
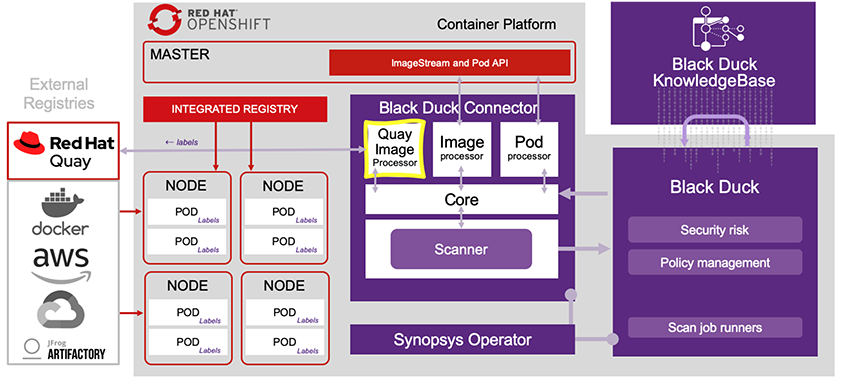
If you’re familiar with the Black Duck Operator and have used synopsysctl to deploy Black Duck and the Black Duck Connector (a.k.a. OpsSight), deploying the Quay processor is a breeze. Follow the Scanning Images in a Red Hat Quay Repository guide in the Black Duck external docs site to set it up. Here are some highlights of the setup:
- The first step is obtaining a token from a Quay OAuth Application in your Quay organization. Using this token, the processor can pull the image and annotate it. You’ll need to add this token into the Black Duck Connector configuration using the flag “–image-getter-secure-registries”.
- Deploying the processor requires two additional flags: “–enable-quay-processor” and “–expose-quay-processor”. These flags create a new service and pod listening on port 3008. The pod listens for any pushed images in the Quay repo to scan and keeps track of any new vulnerabilities affecting the open source components after the initial scan.
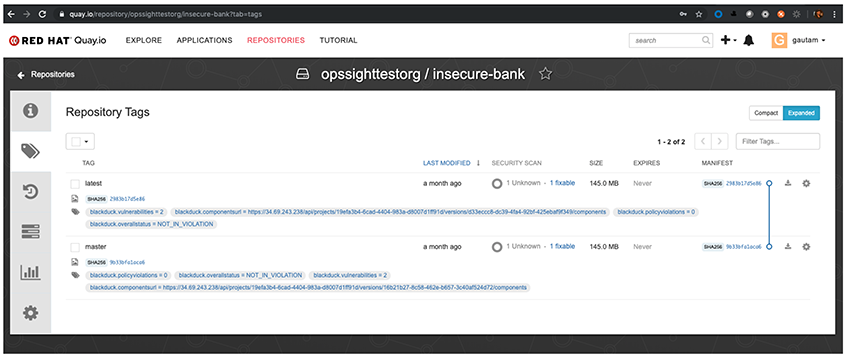
- Once the image is scanned, the pod processor labels images in the Quay processor. The following is a screenshot of what that may look like:
We hope you enjoy using our new container image processor for Red Hat Quay. We welcome feedback, so let us know what you think at partner-solutions@blackduck.com, or open a pull request in the GitHub repository.
Continue Reading
Key findings from “The State of Embedded Software Quality and Safety 2025” report
Aug 26, 2025 | 3 min read
What you need to know about the NIST Secure Software Development Framework
Aug 12, 2025 | 5 min read

