Automotive cyber security standard ISO SAE 21434 specifies requirements for cyber security risk management of road vehicle electrical and electronic systems, including their components and interfaces. It covers engineering for concept, development, production, operation, maintenance, and decommissioning. In our previous blog post we discussed the overall structure of ISO SAE 21434 and took a quick look at three work products that are integral components within the soon-to-be finalized automotive industry standard.
Understanding cyber security assurance levels
Cyber security assurance levels are a classification system that outlines the requirements that should be met to ensure security at each stage of the product life cycle. These levels aren’t technical specifications or requirements directly, but rather they are cyber security goals that are supported with justification and measured against a technical metric. This approach moves with the maturity of the industry and technology available. In terms of the specifications of ISO SAE 21434, these levels must be progressive in nature, meaning the lower levels of assurance must be met in order to progress upward, and may be used as a metric from which to measure road vehicle security.
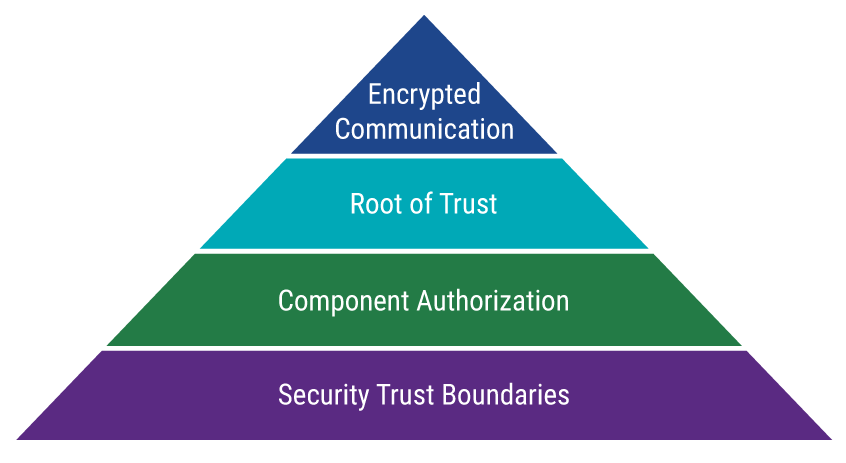
The diagram above shows the progressive nature of the levels of cyber security assurance. In this example, the foundational level of assurance is the establishment of trust boundaries. Similar to the functional safety requirements of ISO 26262, the electrical systems that carry higher requirements of Automotive Safety Integrity Levels (ASIL) are isolated from those with lower requirements. In order to achieve material cost objectives and segregate less-sophisticated electronics, establishing trust boundaries is a prerequisite of any component authorization. Likewise, the authorization of an electrical component is dependent on establishing a root of trust within a system or network. Trust is achieved through a multifaceted approach of authentication and authorization that together can support encryption.
The important takeaway here is that while encryption standards may change, or technologies for establishing boundaries in electrical systems advance, the level of assurance can be met with an independent technical objective. Likewise, the business goal can adapt to this cyber security assurance level as the environment in which road vehicles operate change.
Determining the number of levels needed
Cyber security assurance levels can be used to set objectives and aid in communication outside of security and engineering groups. Their primary use, however, is to assess impacts against a set of given attacks and their associated vectors, specifically the risk of attacks against road vehicles, from negligible to severe.
Attacks may require physical access to the road vehicle or a localized connection that is limited by proximity. The most severe attacks can be conducted remotely through wide area networks or long-range communication methods. Together with your attack vectors, impacts, propagation, and other factors, an assessor can establish a level of confidence associated with an assurance level for each component of a vehicle’s electrical system.
A single assurance level can be assigned to all cyber security goals of a component, or multiple assurance levels can be assigned to each cyber security goal. There is no single mapping of assurance and goals; however, there are appropriate cyber security goals that are unique to each organization’s role within the automotive industry. Goals are typically created with language such as “prevent” or “protect” from a condition, and levels of assurance frame this as a multilayered or “defense in depth” approach. Technical solutions, standards, and requirements should not be included in these goals; their methods should be communicated instead.
Your organization might have a single cyber security goal, or a series of goals, to communicate a roadmap of security maturity for internal and external use. Consider aligning the levels of cyber security assurance to the electrical powertrain roadmap, which provides an opportunity to introduce cyber security maturity. As components gain capabilities for cyber security features, both customers and regulatory agencies will reasonably expect security goal integration.
Tailoring cyber security assurance activities
A single cyber security assurance level can be used to communicate multiple goals of a component, or multiple cyber security assurance levels may be used to communicate each cyber security goal. Simply put, there is a many-to-many relationship between assurance and goals.

The table above illustrates the successive levels of cyber security assurance that would be appropriate for a midsize firm providing application services for road vehicle electrical and electronic systems. It’s recommended that an automotive OEM would have a more exhaustive and broad set of goals and metrics. Likewise, a smaller firm providing a single service may have only a single cyber security assurance goal tied to technical metrics. Tailoring each level to the business model of the components and electrical and electronic systems allows you to set expectations for yourself as well as your suppliers.
Documenting levels of cyber security assurance allows everyone to establish system-level cyber security responsibilities and communicate goals and objectives cross-functionally. Documenting cyber security assurance levels also allows you to provide traceability for supply chain interface agreements with a risk-based approach. From attacks requiring physical access to global remote control of a component or full system, cyber security assurance levels should be met according to degree of impact (ranked from negligible to severe and separated into four categories: safety, financial, operational, and privacy).
Stay tuned for more on ISO SAE 21434
For more information regarding impact calculation and detailed Threat Analysis and Risk Assessment (TARA) coverage within the ISO SAE 21434 standard, look for our next automotive cyber security blog post.
Report

Securing the Modern Vehicle: A Study of Automotive Industry Cybersecurity Practices
Continue Reading
Get the best from AI in software development without risking the worst
Sep 15, 2025 | 5 min read
Contextualizing risk in the AI era
Sep 05, 2025 | 5 min read
What you need to know about the NIST Secure Software Development Framework
Aug 12, 2025 | 5 min read
Black Duck Assist: AI code security assistance in your IDE
Aug 05, 2025 | 3 min read







