Subscribe
Before jumping into the final post within our discussion on vulnerabilities in the MEAN stack, look back at the other four posts within this series discussing MongoDB, Express.js (Core), Express.js (Sessions and CSRF), and AngularJS.
Development mode (Node.js/Express.js)
By default, Express applications run in development mode unless the NODE_ENV environmental variable is set to another value. In development mode, Express returns more verbose errors which can result in information leakage. For example, the error message below returns the full path to the requested file. This also provides an attacker with information about the host system.
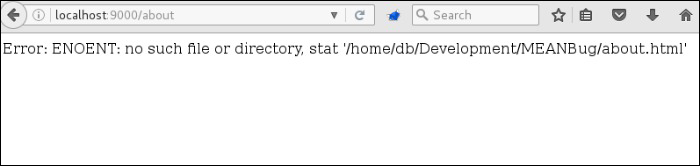
Verbose error leaks full path to requested file
If the NODE_ENV variable is set to ‘production’ (or any value other than ‘development’), the Express server no longer returns the verbose message.
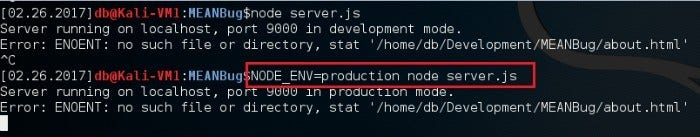
Setting NODE_ENV variable at runtime
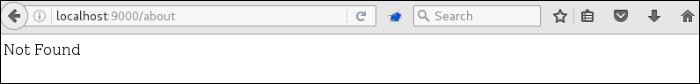
Express returns generic error message
Running Node.js with elevated privileges
On Unix systems, non-root users cannot bind to low-numbered ports. This means that Node.js must be run as root to bind to port 80. However, if we sudo to root to start our web server then our application will be running with unnecessary privileges. To remedy this, invoke the process.setgid and process.setuid methods in the callback function after binding to port 80 as shown below.

Using this approach, we can still start the application with root privileges allowing us to bind to low-numbered ports before downgrading to a less-privileged user ID.
Node Security Platform
A common concern with open source technologies is using vulnerable components. The Node Security Platform (now part of npm) maintains a record of Node.js plugins with known security issues.
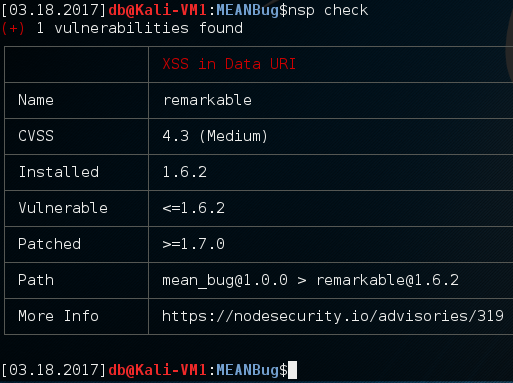
Using 'nsp' command line tool to identify vulnerable Node.js dependencies
Series summary
The vulnerabilities covered during this series are not an exhaustive list. They exhibit some of the more common vulnerabilities encountered when using these technologies, especially with default configurations. Hopefully this information can be used to assist developers in creating more secure applications as well as help security testers identify bugs and flaws within existing applications.
Continue Reading
Contextualizing risk in the AI era
Sep 05, 2025 | 5 min read
Addressing the hidden risks of AI coding tools
Aug 18, 2025 | 1 min read
What you need to know about the NIST Secure Software Development Framework
Aug 12, 2025 | 5 min read




