Black Duck Developer Security Training, powered by Secure Code Warrior, establishes a closed-loop strategy to preclude security risks at the developer desktop and accelerate remediation of issues detected across the software development life cycle (SDLC) and CI/CD pipelines. Establish a complete strategy for secure development with results generated by Coverity, Seeker, and Software Risk Manager, plus integrated training recommendations from the Secure Code Warrior platform. Increase the ROI of your security program with quantifiable reductions of new risks introduced during development.
Relevant, impactful secure coding education
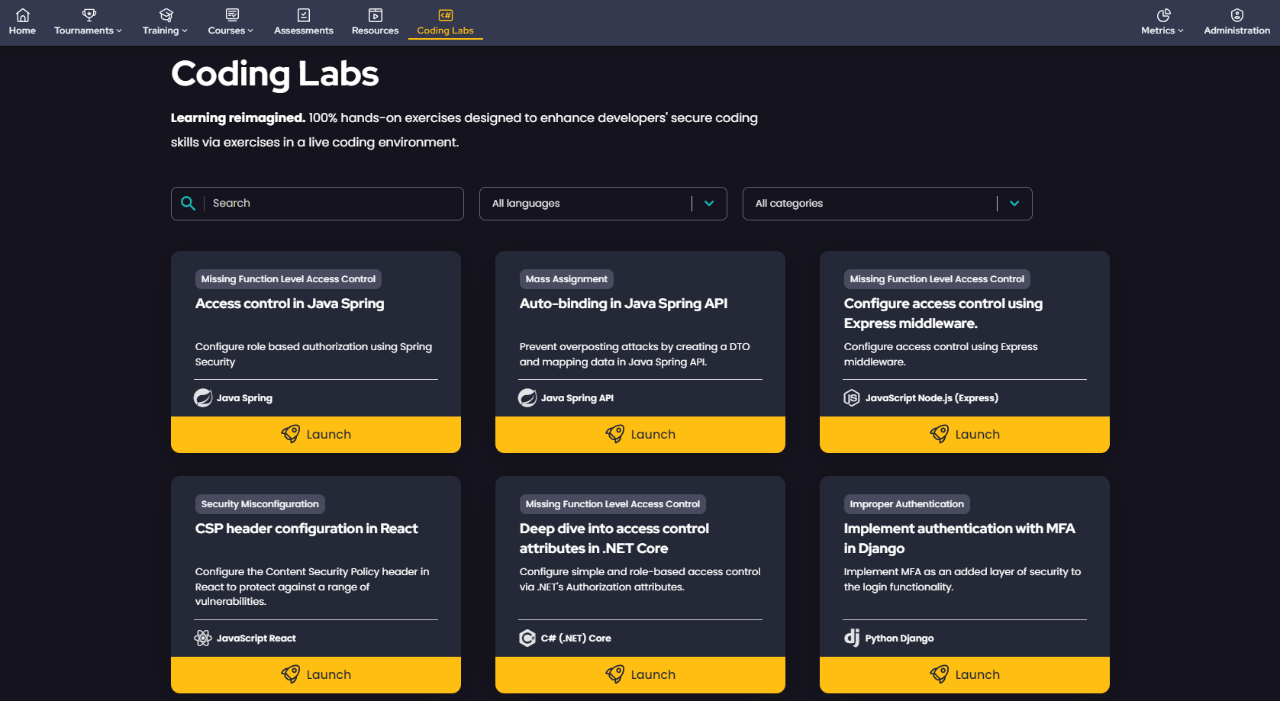
Empower development teams to learn the skills they need to write secure code and support your organization’s DevSecOps initiatives. Leveraging Secure Code Warrior's industry-leading agile learning platform, Black Duck Developer Security Training provides
- Relevant education for development and engineering teams, delivered in interactive microburst formats that don’t derail DevOps workflows
- Curricula that can be tailored to specific technologies, projects, compliance standards, and other business needs
- Risk-relevant training and remediation guidance for issues detected during application security testing with Black Duck application security testing solutions
Integrated security training for DevSecOps
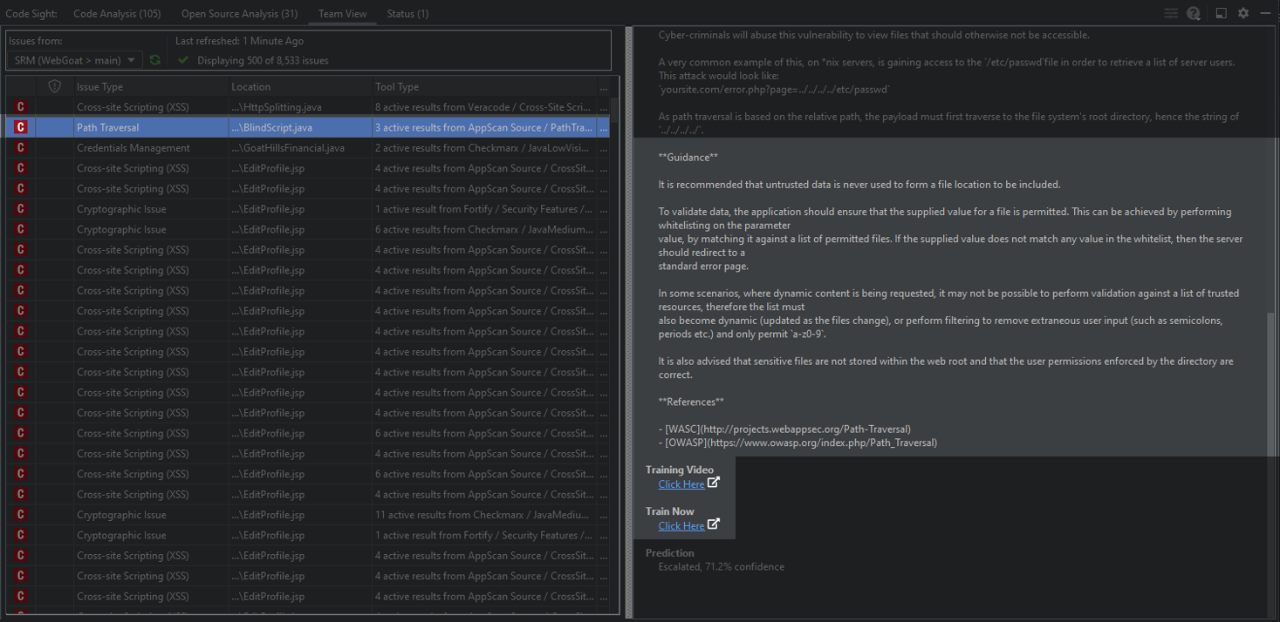
Black Duck and Secure Code Warrior come together to present developers with the most actionable security training, associated with real risks detected by Black Duck application security testing tools.
- Risk-relevant secure coding education teaches developers to fix issues detected by Coverity, Seeker, and Software Risk Manager
- Policies can be configured to highlight the most important risks to your business and prescribe training to avoid introducing them
- Developers have instant access to security training associated with real risks in their projects via the Code Sight™ IDE plugin
Interactive security training for developers
Enhance your security posture and maintain development velocity with resources to foster developer security awareness and capabilities, including
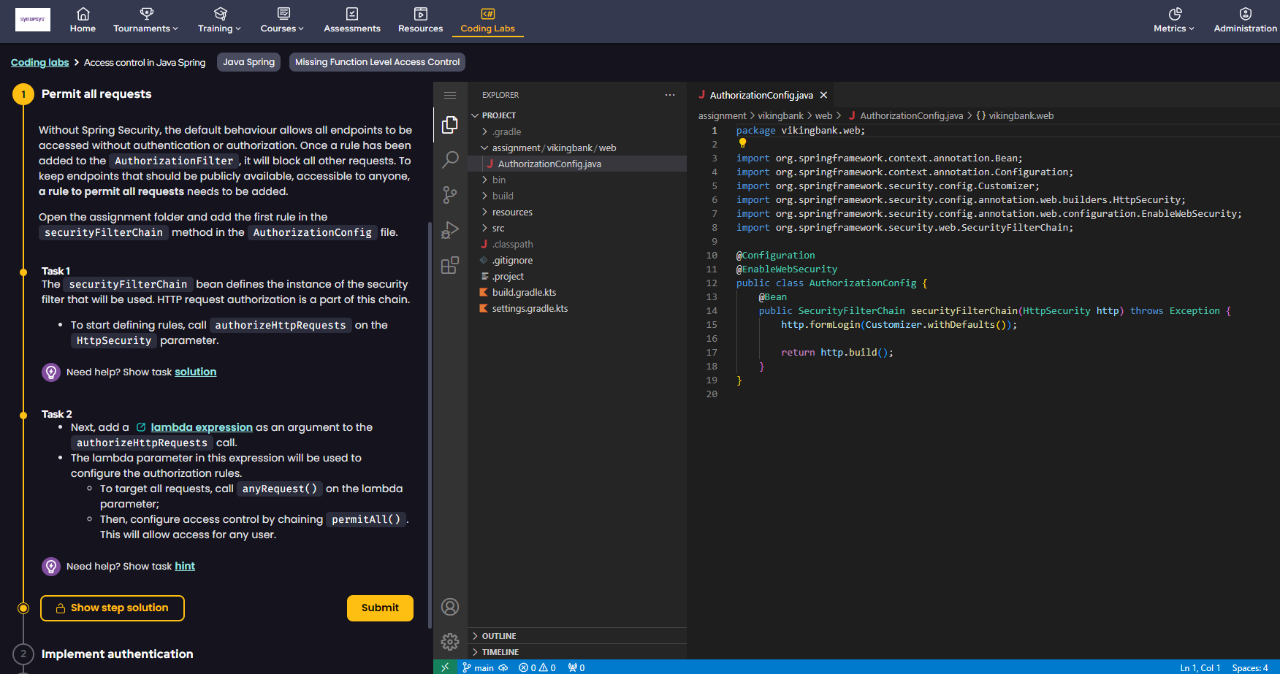
- Clear and detailed courses that use interactive learning formats so developers can learn, test, and apply their knowledge in the context of real work they are already doing
- Step-by-step guided walkthroughs to help developers understand vulnerabilities and insecure coding patterns
- The most expansive library of security topics and concepts available today, tailored to developers of diverse skill levels, from beginner to security champion
Engaging mechanisms to hone developer security skills
Developers are an organization’s first line of defense when it comes to averting exploitation and infiltration of vulnerable applications. Drive engagement and retention among development teams with
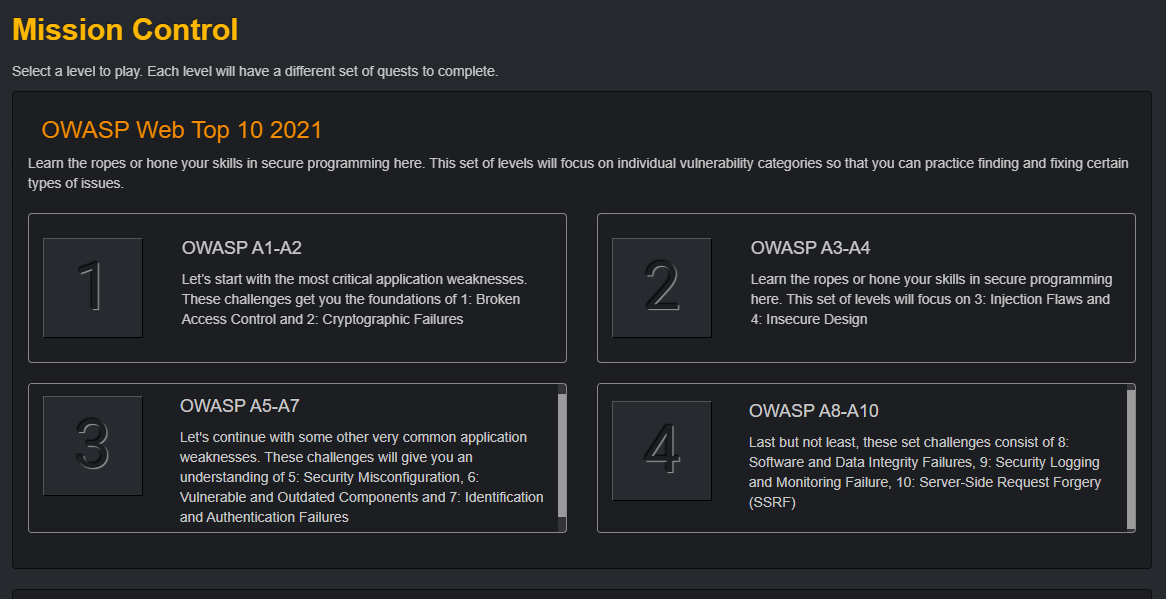
- Immersive coding simulations that send developers on missions to practice secure coding and offensive security tactics in a risk-free environment
- Challenge-based exercises in which developers analyze real-world scenarios, identify problematic code, and choose the best remediation tactic to earn points and advance in team leaderboards
- Hands-on coding with real-time feedback in a secure, browser-based IDE to foster security capabilities with contextualized feedback and coaching while developers code