Threat modeling identifies risks and flaws affecting a system. Here are 5 primary activities to perform when creating or updating a threat model.
Threat modeling identifies risks and flaws affecting a system. A thorough analysis of the software architecture, business context, and other artifacts (i.e. functional specifications, user documentation) allows practitioners of the threat modeling process to discover important aspects of the system—security-related or not—and synthesize an understanding of the system that may not yet exist within the organization. There are five primary activities that need to be performed when creating or updating a threat model:
1. Define scope and depth of analysis
The first step in shaping a threat model is to define the scope and depth. Once a reasonable scope is determined with stakeholders, it needs to be broken down in terms of individual development teams so they are able to develop a model of the software.
2. Gain an understanding of what is being threat modeled
Diagramming the system structure is critical. This creates a solid visual understanding of the system. The component diagram below illustrates the major components of the system and the interactions between those components.
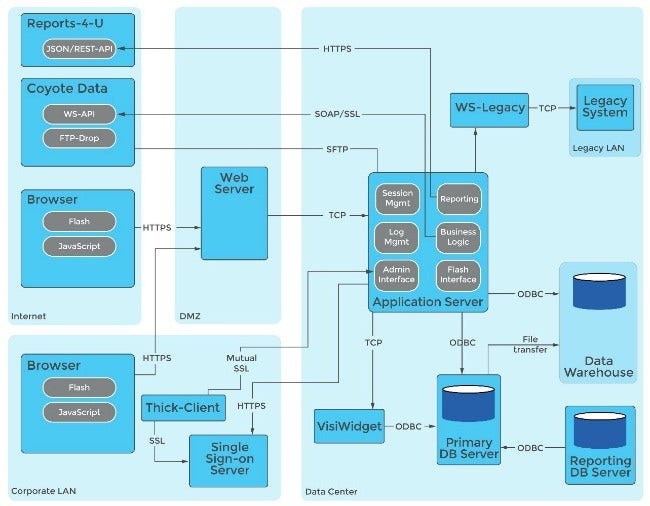
Components identified in this diagram include the application server, a legacy system, data warehouse, thick client, primary database server, and a single sign-on server.
3. Model the attack possibilities
Identify the assets, security controls, and threat agents. Once identified, mark their locations as the diagram below illustrates.
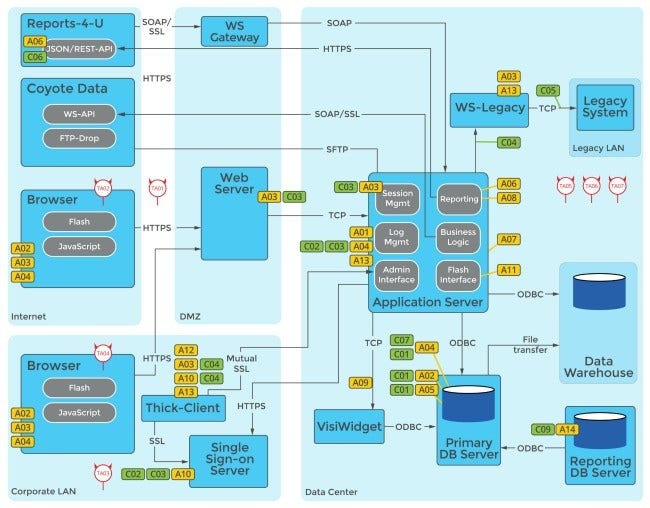

4. Interpret the threat model
Now that you have created a threat model, it’s time to interpret it. This interpretation will allow you to generate a traceability matrix to drive other security activities (including secure code reviews and penetration tests) in a risk-based fashion. Produce a list of potential attacks by asking questions like:
- Is there any path where a threat agent can reach an asset without going through a control?
- For any security control along each of those paths:
- What must a threat agent do to defeat the control?
- Can a threat agent defeat the control currently?
5. Create a traceability matrix to record missing or weak controls
A traceability matrix examines a threat agent. This agent may attempt to compromise an asset by conducting an attack somewhere along the attack surface. Consider what the attack goal could be and how it could impact the target. To mitigate an attack, a control is put in place to establish an acceptable level of risk. Repeat this process for all threat agent/asset combinations.
To create a traceability matrix, consider the threat agents and follow the control path. If you reach the asset without going through a control, you may have discovered a potential attack. If you went through a control, consider whether the control would halt a threat agent and whether that threat agent may have methods to bypass the security control. This is where a knowledge of actual attacks is essential.
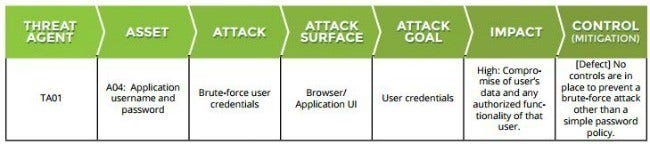
Although the threat modeling process is simple, it takes time and repetition to become proficient at it. A highly detailed traceability matrix can ensure a thorough and complete threat model. Consider the following additional column categories to achieve this holistic approach:
- Skill
- Motivation
- Attack vector
- Discoverability
- Probability
With experience, you’ll be able to develop a simplified traceability matrix. This allows you to properly track threat information through the requirements, design, and testing phases of the SDLC without as much documentation.
eBook

Six Steps to Effective Threat Modeling
Continue Reading
Get the best from AI in software development without risking the worst
Sep 15, 2025 | 5 min read
Contextualizing risk in the AI era
Sep 05, 2025 | 5 min read
What you need to know about the NIST Secure Software Development Framework
Aug 12, 2025 | 5 min read
Black Duck Assist: AI code security assistance in your IDE
Aug 05, 2025 | 3 min read







