Subscribe
With the evolution of the Internet of Things (IoT), there are billions of devices in the world today. Everything is becoming a computer—your thermostat, stove, refrigerator, washer, dryer, vehicle, door locks—even things like lawn mowers and vacuum cleaners. From robots on the factory floor to speakers in your living room, connected devices are ubiquitous.
The growth of IoT
Indeed, the number of connected devices has exploded in recent years to an estimated 30 billion. And that growth shows no sign of slowing.
What will this mean for society? If the state of security and privacy of connected devices continues its current trajectory, it could be a dystopian future. “Smart” devices could be riddled with vulnerabilities that hackers will exploit to steal credentials and identity, and extort or blackmail users by threatening their physical safety. Critical infrastructure like electricity grids and telecommunications networks could be compromised, with major disruptions to consumers. Expanded data collection by Big Tech will make smartphones even more intrusive surveillance trackers than they are now.
The need for IoT security
However, there is an alternate possible reality that diverges from this scenario. It could be a world where the software that powers all those devices has security and privacy controls built into it. The software could also be designed to allow updates and patches as vulnerabilities are discovered and threats evolve.
It won’t make IoT devices bulletproof—nothing will—but it could make them much more resilient. Better software security could be the digital version of seatbelts, airbags, antilock brakes, lane assist, and other safety features in cars. They don’t eliminate accidents, but they help drivers avoid them and offer more protection when they do happen.
And that’s possible. The tools, technology, and methods exist to make the software running connected devices much more secure and robust. They just aren’t being adopted nearly as much as they should be.
One reason for that has been widely reported: users often neglect or overlook security in their purchasing decisions. They are primarily focused on the features and prices of devices. Security is barely an afterthought—it’s not yet a “differentiator” for consumers. Therefore, manufacturers produce devices with cool features and a good price without thinking much about IoT security.
Another reason is the mismatch between the lifespan of large appliances and the lifespan of newer, smaller mobile devices. Stoves, refrigerators, dishwashers, and clothes washers and dryers have a lifespan of perhaps 10 years, whereas phones and laptops will get updated or replaced every year or two. Manufacturers that have expertise building longer-lasting hardware often don’t have the skills to design software security into their products.
Building security into the SDLC
It will take a paradigm shift to realize the safer future. Creating a future with more-secure IoT devices requires building security into the software development life cycle (SDLC). Here’s a brief look at each stage of the SDLC, and ways to build security into it.
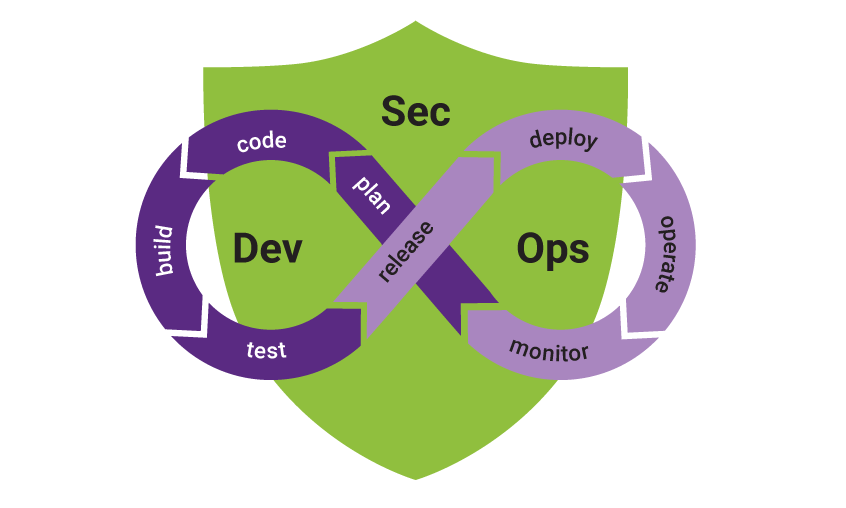
Plan
This stage includes defining requirements for what the software will do, and estimating the costs, scheduling, procurement needs, and staff needed to implement it.
But it should also include a security component: threat modeling. Sometimes referred to as “thinking like a hacker,” the goal is to go beyond the standard list of known attacks and identify possible threats that are unique to how your system is built or what it is intended to do.
Good threat modeling includes highlighting assets, threat agents, and controls to determine which components attackers are most likely to target, and then creating remediation measures to reduce those threats.
There are multiple benefits of threat modeling, but among the most important is that it can save time and money. Looking for potential problems early, before a single line of code is written, can catch design flaws that traditional testing and code review might miss. Fixing or avoiding them early is cheaper and faster.
Code
This stage involves writing software code to fulfill the design requirements. Static application security testing (SAST) tools help developers find and fix security and quality defects as they write code. Best-of-breed tools run fast and incremental analysis in the background to minimize disruption. Developers get real-time results, including CWE information, and remediation guidance directly in the IDE.
Build
Modern software is rarely simply written by a team of developers. It’s assembled. Some components are proprietary, but others are from commercial or open source libraries.
Test
This is no longer a separate stage when a security team probes software for vulnerabilities at the end of the SDLC. Testing needs to be pervasive, from threat modeling before coding begins all the way through to production. It requires multiple testing tools, including static, dynamic, and interactive testing; fuzz testing throughout development; and software composition analysis (SCA) to find vulnerabilities or licensing conflicts with open source code. It also requires penetration testing (more on that below) before the software is deployed.
If there are different protocols communicating with your devices, fuzz testing will ensure your overall system is secure and robust. Common protocols include internet protocols like IPv6 or short-range protocols like Bluetooth, with newer protocols like Thread for low-power and low-latency usage becoming more widely deployed.
Finally, penetration testing uses a variety of testing tools and manual tests to find and eliminate business-critical vulnerabilities in running web applications and web services, without the need for source code. It is a “last chance” to catch and fix significant vulnerabilities before exposing those applications and services to the wider world, where malicious attackers will be looking for ways to compromise and exploit them.
Obviously, it’s much better to have testers find defects before threat actors do. Black Duck offers two levels of pen testing, based on the risk profile of each tested application. The essential level includes automated scans and manual testing. It focuses on exploratory risk analysis (e.g., anti-automation, complex authentication). The standard level includes essential services plus testing time and effort to explore business logic, which covers attacks outside a predefined list or those that may not have been considered otherwise (e.g., business logic data validation and integrity checks). It also includes a manual review to identify false positives and a readout call to explain findings.
Black Duck Software Risk Manager can manage all those AppSec analysis tools without slowing development down. By using predefined risk policies set by each organization, it triggers the right security tests at the right time. The result is the right information delivered to developers and security teams to ensure compliance with their policies across all pipelines. By unifying policy, test orchestration, correlation, prioritization, and built-in SAST and SCA engines, organizations can streamline their security activities across the enterprise.
Security teams need to also consider the deployment model for their application security testing tooling. Traditionally, firms have opted for on-premises installations to ensure control over their data and infrastructure. With the rise of cloud computing, many organizations are embracing a software-as-a-service (SaaS) model in which their applications and data are hosted in the cloud. The main benefit of a cloud deployment is the reduced costs from having less physical hardware and infrastructure to maintain, along with the associated IT teams to configure on-premises tools. In addition, using a SaaS application security tool means your security overhead can scale with your business elastically.
Black Duck Polaris™ Platform is an integrated, cloud-based application security testing solution optimized for the needs of development and DevSecOps teams. The Polaris platform brings Black Duck market-leading security analysis engines together in a unified platform, giving you the flexibility to run different tests at different times based on application, project, schedule, or SDLC events. With Polaris fAST Static, you can find and fix security defects in proprietary code and infrastructure-as-code (IaC) templates with fast incremental scanning that delivers accurate results and dramatically reduces scan times. With Polaris fAST SCA, you can identify vulnerabilities in your application’s software supply chain with detailed Black Duck® Security Advisory (BDSA) guidance to help you assess severity and impact as well as potential workaround and upgrade options. In addition, the Polaris platform enables you automate scanning and policy with the DevOps tools you use today. This includes source code managers like GitHub and GitLab, continuous integration tools like Jenkins, and issue-tracking tools like Jira.
Release
This stage involves the development team packaging, managing, and deploying releases across different environments.
Deploy
This is the stage when software is released into the production environment.
Operate
This is the stage when software is used in the production environment.
Monitor
During this stage, the team tracks the performance of the software, including system performance, user experience, new security vulnerabilities, and analysis of bugs or errors in the system. Additionally, updates or patches are pushed out to users to close vulnerabilities or respond to new threats.
Notice that an effective SDLC doesn’t end when a product is shipped; it continues through that product’s useful life. Although “building security in” during development will minimize bugs and other defects, the reality is that there is no perfect software. So securing IoT devices means maintaining them.
Online learning for developers
It takes more than automation for security to keep pace with the speed of development. Humans still have to run the show. Building secure software at the speed of development requires giving developers not only the tools they need, but training as well—something a good eLearning program can provide.
Secure Code Warrior delivers impactful security training for DevSecOps with interactive eLearning and hands-on labs, enhancing developers' secure coding capabilities to fix issues detected by Black Duck AST tools and prevent new issues directly at the developer desktop. Our portfolio of AST tools is integrated with Secure Code Warrior for easy triage and resolution of vulnerability findings.
Improving IoT security
- As we noted at the start, there is no way to build perfect software. It doesn’t make sense to try, since that would likely mean never releasing a product.
- But it’s possible to avoid being low-hanging fruit, with an effective software security initiative and an SDLC that embeds security into software throughout that process. Most attackers are looking for easy targets. If your apps, services, and networks are difficult to breach, chances are good that they will move on.
- You may never know the exact ROI of your security program. But that’s a good outcome—because you really don’t want to know.
Continue Reading
Contextualizing risk in the AI era
Sep 05, 2025 | 5 min read
Addressing the hidden risks of AI coding tools
Aug 18, 2025 | 1 min read
What you need to know about the NIST Secure Software Development Framework
Aug 12, 2025 | 5 min read





